Neon Auth is Here: Get Authentication in a Couple of Clicks
Spin up authentication fast while avoiding lock-in
We’re excited to announce Neon Auth, a fully managed authentication solution tightly integrated into the Neon platform. It now takes seconds to provision an auth solution directly from the Neon console; once set up, your user profiles automatically sync to your database.
The best part: if you ever decide to move away from Neon, you can transfer ownership of your managed auth configuration to an external account just as easily as you set it up. And if you ever decide to change auth providers, all your auth data lives in your database, which makes any migration much easier.
Authentication in seconds, with full portability
Behind the scenes, Neon Auth works as an automated provisioning and synchronization layer between an authentication provider (Stack Auth, an open-source auth provider) and your Neon database. Because it’s fully managed by Neon, it keeps user profiles in sync automatically without requiring any extra code, background jobs, or webhooks.
Coming soon
To set it up for your project, simply open the Auth section in the Neon console and click Setup Stack Auth:
This managed layer approach prevents vendor lock-in:
- When you click “Setup Stack Auth”, a Stack Auth project is automatically provisioned for you.
- You can claim ownership of this project at any time by clicking “Transfer ownership”, and it will be moved to your Stack Auth account. And the best part is that the user synchronization feature will continue to work.
That means you’ll always retain full control over your authentication layer—even if your deployment changes in the future.
If you’re already a Stack Auth user or if you need additional customization (like choosing a custom project name), you can also use the “Manual setup” option. During this process, you’ll simply select the Stack Auth project you want to integrate with Neon Auth. Once connected, Neon will keep your user data synchronized automatically.
Before Neon Auth
Let’s now dig a little deeper into why we’ve built Neon Auth.
Imagine you’re building a SaaS application that allows teams to collaborate on projects. Users sign up and authenticate through an external authentication provider. Your Postgres database stores projects, tasks, and user permissions, with a data model that looks something like this:
userstable: Stores user information (id,email,name, etc.)projectstable: Stores project details (id,name,created_by)user_rolestable: Defines user permissions (user_id,project_id,role)
Once you ship your application, what needs to stay in sync between your authentication provider and the Postgres database?
- User creation. When a new user signs up, their profile should be available in Postgres.
- User updates. If a user changes their email or display name in the auth provider, the update should reflect in the database.
- User deletion. If a user is deleted or disabled in the auth provider, access should be revoked immediately.
- Role changes. If the auth provider manages user roles (e.g., team owner, editor, viewer), those permissions must sync with the database.
You would typically handle this sync manually using one of:
- Webhook listeners (listening for changes from the authentication provider)
- Background jobs (running periodic tasks to fetch and update user data)
- API calls on every login (querying the auth provider when a user logs in to ensure data is fresh)
This is a lot of extra work. Not only do you have to manage authentication and Postgres separately, but you also have to:
- Write and maintain sync logic
- Handle API failures and rate limits: If the auth provider’s API is slow or temporarily down, your user sync breaks
After Neon Auth
Neon Auth removes this complexity:
- It manages authentication for you, provisioning a fully configured auth provider (via Stack Auth for now) in just a couple of clicks
- It exposes user data as a standard Postgres table (
neon_auth.users_sync), keeping it continuously in sync with the auth provider (this prevents lock-in)
Now, instead of managing custom sync logic, you can just query your database like any other table:
SELECT * FROM neon_auth.users_sync;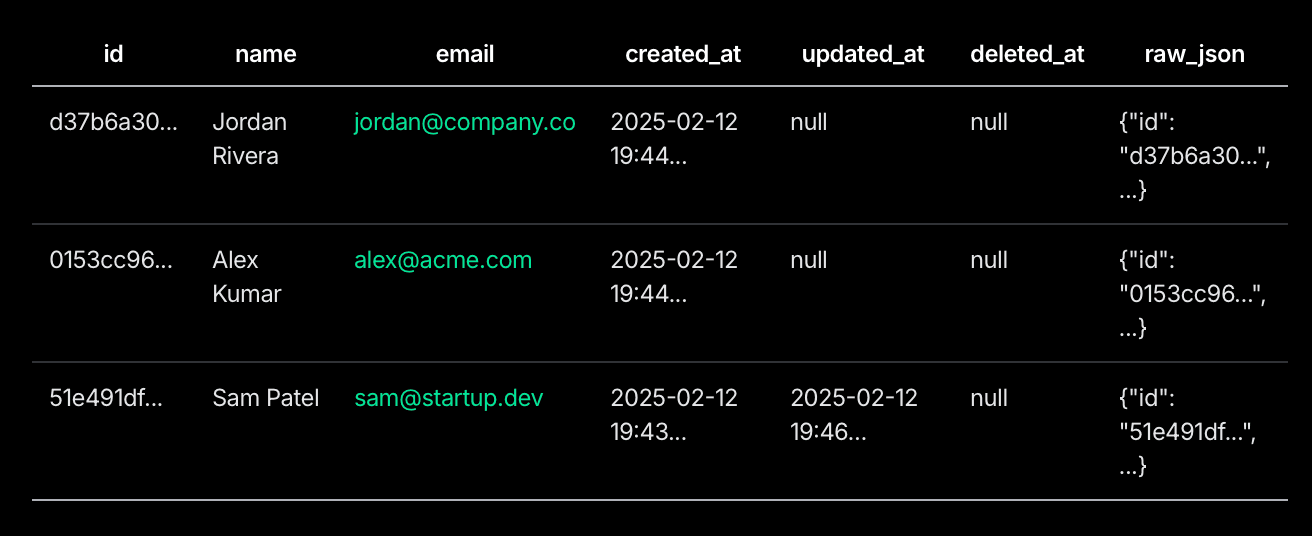
How is this helpful?
Since your auth data is in your Neon database, you can easily reference it with JOINs. This data can also be really useful for building admin consoles and dashboards, and for cron scripts which are easier to hook up to Postgres than to your auth provider’s REST API.
With Neon Auth, authentication and user data management are simplified. No more custom sync scripts. No more webhooks. Just SQL.
Ensuring fresh user data
Neon Auth synchronizes user profiles from the underlying authentication provider to your Postgres database asynchronously: updates happen with a short delay (should be sub-second in the vast majority of instances), so there is a very brief window where a newly authenticated user may not yet exist in the neon_auth.users_sync table. How to handle this?
It’s simple: Use LEFT JOIN instead of INNER JOIN for queries that depend on user data.
SELECT todos.*, neon_auth.users_sync.name
FROM todos
LEFT JOIN neon_auth.users_sync ON todos.user_id = neon_auth.users_sync.id
WHERE neon_auth.users_sync.deleted_at IS NULL;Using LEFT JOIN ensures the main query still executes, even if the user record hasn’t arrived yet. Once the user profile is synced, the name column will automatically populate.
Get started
Auth is available to all Neon users, currently in Beta. Check out our documentation for details, and jump into to the console to set it up.
Not yet a Neon user? Sign up for our Fee Plan here.